Free SSL certificates for test and development environments
If you have developed an application and are now facing a challenge of configuring your SSL in test environments, this article is just for you. Read on to learn how to:
- provide your environments with LetsEncrypt certificates
- automate their generation and renewal
- elegantly circumvent the limitations of test and development environments.
Many an application developer faces a challenge when configuring SSL in test environments. Paid certificates unnecessarily increase the development cost. Wildcard certificates are often unavailable or the client/ the owner does not allow their use outside his production systems. Self-signed certificates, on the other hand, spoil impressions at test application presentations.
LetsEncrypt is a free of charge certification authority for creating and renewing free X.509 certificates. Offered since 2016, it has become widely popular and has been rolled out in many implementations, integrating it with popular WWW servers and applications terminating SSL.
LetsEncrypt certificates are very useful in development and staging environments. Due to their short life (90 days), they necessitate automation, which happens to be difficult due to a non-homogeneous environment often inaccessible from the Internet.
An impediment may also be posed by the applicable limits, which enable – at the time of writing – a maximum of 20 domain certificates to be generated per week.
In this article, we will take a look at the methods which can be applied to circumvent these limitations, ensure encrypted communication regardless of whether the environment is accessible from the Internet or not, and which application terminates SSL. We will also present a pseudocode for implementation and solutions which can be used to roll out your own solution.
Methods of authentication (challenge types)
A standard method of validating certification requests is the http-01 ACME protocol, which uses verification by means of a temporary file with the name and content specified by the ACME server (e.g. LetsEncrypt.org). This method is leveraged by most WWW server certification automation tools, certbot being the most popular of them.
This solution has two major drawbacks:
- The implementation method depends on the WWW server used.
- External facing applications may interfere with the web application used – if, for example, you have an automated redirection adding a www prefix to the address, you will have to switch it off for the time of certificate generation without a prefix.
- The certified website must be available on the Internet, which is often unviable for purely development environments.
It is possible to carry out validation without initiating traffic to the WWW server. This is provided by the dns-01 ACME mechanism. The authentication is performed by means of TXT records in DNS, hence:
- It can be used regardless of the WWW server used.
- No interference with a web application is possible.
- The certified website does not have to be open to the Internet, and what’s more – the certified domain does not have to exist at all, as long as you have control over the parent domain.
Illustrative architecture
The diagram below presents a communication model in certification performed by means of the dns-01 method:
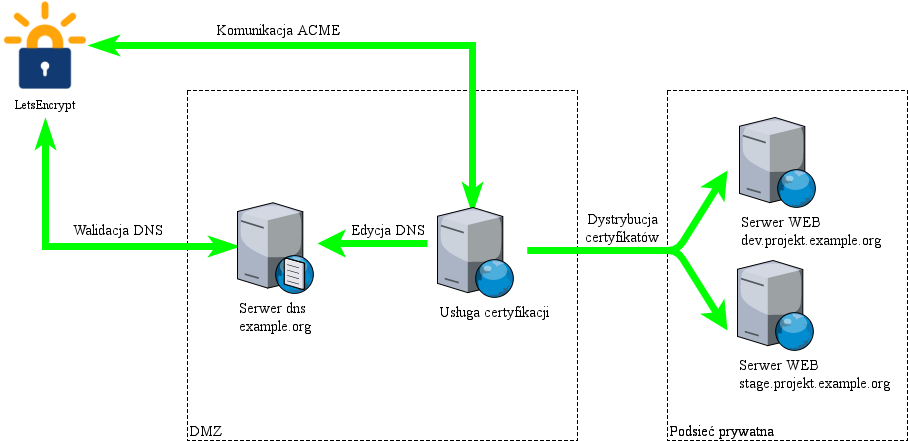
Only the DNS server for the service of the desired domain and certification service are directly involved in the process.
Any service can serve as the DNS server as long as it enables the dynamic editing of records. It can, for example, be a DNS server serviced by API (Amazon Route53 or CloudFlare), and any server servicing RFC2136 protocol (Microsoft DNS, Bind 8, or Bind 9).
The certification service initiates communication with LetsEncrypt, carrying out validation by editing servers and – upon receipt of certificates – it installs them on web servers, as well as reloading them with a view to downloading data.
What is worth noting, however, is that certification service may work separately and service all the WWW servers, but it can also be installed in each WWW server as a separate process – as long as the policy of traffic in the private subnet allows outbound traffic.
Implementation
The pseudocode of certification service may be as follows:
domeny=pobierz_liste_domen()
challenge=zainicjuj_komunikacje_letsencrypt(domeny)
wprowadz_zmiany_w_dns(challenge)
while sprawdz_challenge(challenge):
time.sleep(5)
zapisz_certyfikat_i_klucz()
przeladuj_serwer_www()
domeny=pobierz_liste_domen()
challenge=zainicjuj_komunikacje_letsencrypt(domeny)
wprowadz_zmiany_w_dns(challenge)
while sprawdz_challenge(challenge):
time.sleep(5)
zapisz_certyfikat_i_klucz()
przeladuj_serwer_www()If your server services RFC2136, you can use the nsupdate tool for updates:
$ nsupdate -d -k klucz
server dns.example.org
zone example.org.
update delete _acme-challenge.dev.projekt.example.org.
update add _acme-challenge.dev.projekt.example.org. 3600 TXT “LOREM IPSUM”
sendor rely on many available implementations, e.g. dns modules available in Python:
def doDNSUpdate(server, zone, record, value):
keyRing, keyAlgo = getDNSKey(DNS_KEYFILE)
update = dns.update.Update(zone, keyring=keyRing)
if value is not None:
update.replace(record, 5, "TXT", value)
else:
update.delete(record)
dns.query.tcp(update, server)
If your DNS server does not service dynamic changes in DNS, you can always try to use their API – it may prove necessary in the case of AWS Route53, for example.
The implementation of the ACME protocol may prove time consuming and as such it is worth relying on ready-made solutions, e.g. acme-tiny.
To wrap up…
Implementing automated website certification is particularly useful in mixed development environments where many projects are developed in diverse technologies. The solutions, as proposed, can be applied regardless of whether the application is built on Java, Ruby on Rails or PHP. Quite importantly, they don’t require opening up development environments to the world.
Establishing a separate certificate generation service is also a way to overcome the capacity limitations of LetsEncrypt, provided you allow the use of one certificate with an SAN extension for multiple subdomains. This helps increase the maximum number of certificates by approx 100-fold.
A properly prepared certification service can be quickly put in the existing or new environment, ensuring an automatic supply of secure SSL certificates.







